
shared secrets are not secret
all common authentication methods require some form of text-based user input
users must recall and replay strings of text
text is hard for users, easy for hackers
creating and remembering lots of complex strings is difficult
too many • too complex • too infrequently used • too easily compromised

cryptographic salt is limiting
salting of low-entropy text strings is required to increase randomness and avoid collisions
consequently, salt must be known only to the issuer, which causes a bi-lateral constraint

bi-lateral verification is weak
virtually all authentication methods rely on a bi-lateral (two-party) exchange
attackers only need a single point of compromise to steal credentials
.

trust erodes over time
even so-called strong authenticators suffer erosion of trust over time
trust erodes during a session, and even moreso over multiple sessions
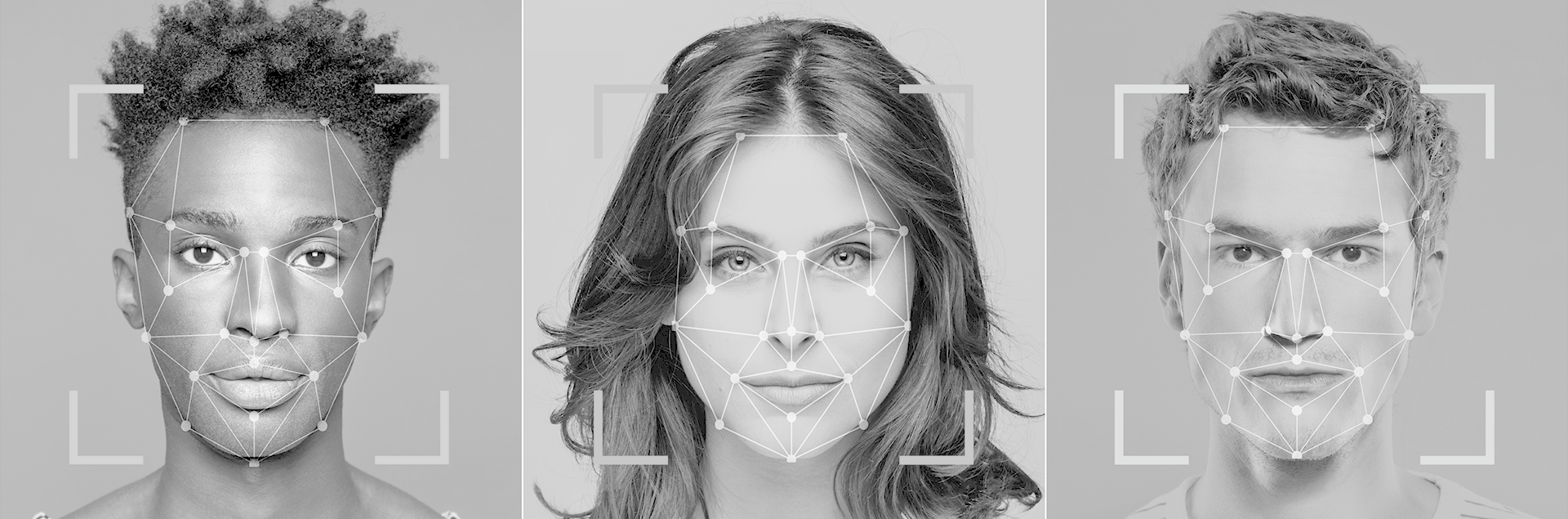
biometrics invade privacy
adding biometrics increases risk of catastrophic privacy breaches
biometrics are impossible to reset if compromised

what if...
...we could thwart user-targeted and service-targeted credential attacks?
The dream is real...
